- Main
disadvantage of
Extensible Hashing:
- The size of the
bucket array
will double each time
the parameter i incraeses by 1
- This exponential growth rate is too fast
- The size of the
bucket array
will double each time
the parameter i incraeses by 1
- Properties of the
Linear Hashing technique:
- The growth rate of
the bucket array will be
linear
(hence its name)
- The decision to
increase the
size of the
bucket array is
flexible....
A commonly used criteria is:
- If (
the average occupancy per bucket
>
some threshold
) then:
- split one bucket into two
- If (
the average occupancy per bucket
>
some threshold
) then:
- Linear hashing uses overflow buckets .....
- The growth rate of
the bucket array will be
linear
(hence its name)
-
Recall the
bucket doubling
technique
used in
Extensible Hashing:
- Before
doubling
the logical hash table:

-
After
doubling
the logical hash table:

Notice:
- We increased the
logical hash table
size
to
implement:
- A mapping of additional hash keys to the physical hash table
Graphically:

Idea:
- If
a hash key
maps to
an old (existing)
physical hash entry:
- You don't need
a new block pointer to
perform the
mapping
- Because you can used the existing block pointer to perform the mapping !!!!
- You don't need
a new block pointer to
perform the
mapping
- We increased the
logical hash table
size
to
implement:
- Before
doubling
the logical hash table:
-
How to
re-use
the
existing
block pointers
to
double
the (logical) hash table:
- Define the following
function:
Suffix-1( x ) = x − 2i where i = ⌊ log2( n ) ⌋What is the Suffix-1( ) function:
x (bin) | i = ⌊ log2( n ) ⌋ | 2i | x - 2i -----------+----------------------+------+---------- 2 ( 10) | ⌊ log2( 2) ⌋ = 1 | 2 | 0 ( 0) 3 ( 11) | ⌊ log2( 3) ⌋ = 1 | 2 | 1 ( 1) 4 ( 100) | ⌊ log2( 4) ⌋ = 2 | 4 | 0 ( 00) 5 ( 101) | ⌊ log2( 5) ⌋ = 2 | 4 | 1 ( 01) 6 ( 110) | ⌊ log2( 6) ⌋ = 2 | 4 | 2 ( 10) 7 ( 111) | ⌊ log2( 7) ⌋ = 2 | 4 | 3 ( 11) 8 (1000) | ⌊ log2( 8) ⌋ = 3 | 8 | 0 ( 00) 9 (1001) | ⌊ log2( 9) ⌋ = 3 | 8 | 1 ( 01) 10 (1010) | ⌊ log2(10) ⌋ = 3 | 8 | 2 ( 10) 11 (1011) | ⌊ log2(11) ⌋ = 3 | 8 | 3 ( 11) 12 (1100) | ⌊ log2(12) ⌋ = 3 | 8 | 4 (100) 13 (1101) | ⌊ log2(13) ⌋ = 3 | 8 | 5 (101) 14 (1110) | ⌊ log2(14) ⌋ = 3 | 8 | 6 (110) 15 (1111) | ⌊ log2(15) ⌋ = 3 | 8 | 7 (111)Conclussion:
Suffix-1(x) returns the suffix of x after removing the leading 1 bit in x
- We can use the
Suffix-1( )
function to
map
between
logical hash buckets and
physical hash buckets:

So we don't need to use a block pointer for the logical hash index x if:
- Bucket[ Suffix-1( x ) ] = (points to same block as) Bucket[ x ] !!!
- Define the following
function:
- Consider the following
4 buckets:

- We double the
number of
logical hash buckets
by using the
Suffix-1( ) function:

Fact:
- We still have 4 physical hash buckets
- We can (gradually)
add
a new physical hash bucket
as follows:
-
Allocate a
new
disk block
(to store the hash keys):
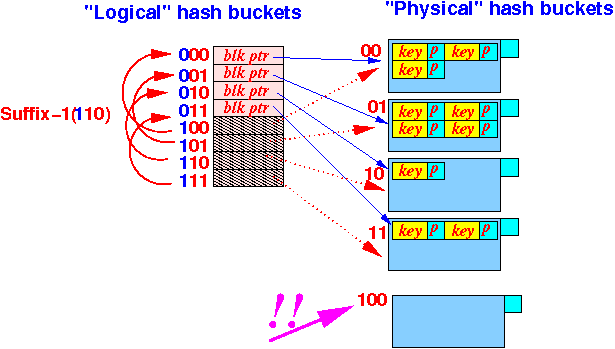
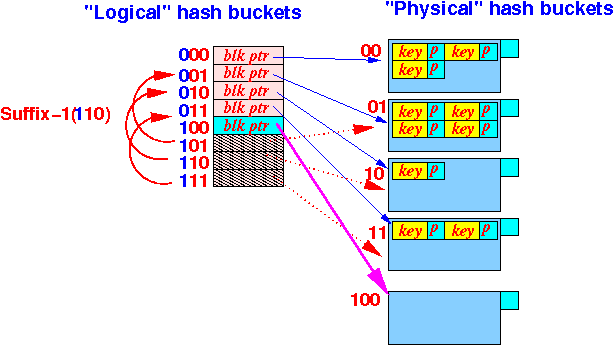
- Allocate
a new
Bucket pointer
in the array and
make it point
to the new hask bucket (disk block):
And: we must re-hash all keys in the "related" bucket:
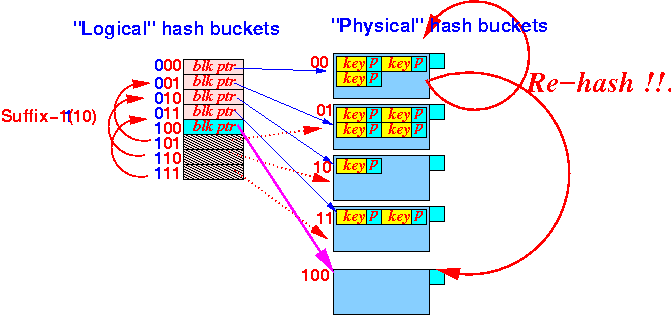
Notice that:
- We still use the
Suffix-1( )
to map
the
"ghost" (= non-existant) buckets !!!
(To allow us to find the hash keys --- just like in Extensible hashing !!!)
-
Allocate a
new
disk block
(to store the hash keys):
- Parameters used in
Linear Hashing:
- n =
the
number of
buckets
that is
currently in use
Note:
- The n buckets are
number as:
0, 1, 2, .... , (n−1) // In binary
- The n buckets are
number as:
- The
derived parameter
i:
i = ⌈ log2( n ) ⌉The value of i changes with n as follows:
(#buckets) (largest bucket index) n n-1 (binary) i = ⌈log(n)⌉ --------------------------------------------------- 2 1 ( 1) 1 ^ 3 2 ( 10) 2 4 3 ( 11) 2 ^^ 5 4 ( 100) 3 6 5 ( 101) 3 bits 7 6 ( 101) 3 8 7 ( 111) 3 ^^^ 9 8 ( 1000) 4 10 9 ( 1001) 4 bits 11 10 ( 1010) 4 ^^^^ ....
Observation: The range of hash bucket index = [0 .. (n−1)] In order to express (n−1) as a binary number, you need i bitsIn other words:
- i = number of bits used in the RandomNumGen( ) to hash into a hash table of size = n
- n =
the
number of
buckets
that is
currently in use
- Hash function used in
Linear Hashing:

Hash index:
- Hash index = the last i bits in the RandomNumGen( key ) value.
- A
hash bucket
in
Linear Hashing is
a
chain of
disk blocks:

- Important Note:
- A hash key value can be > (n − 1) !!!
Example:
- Suppose
n = 9 ( 1001 binary )
A hash key value can be > 9
Example: (1111)
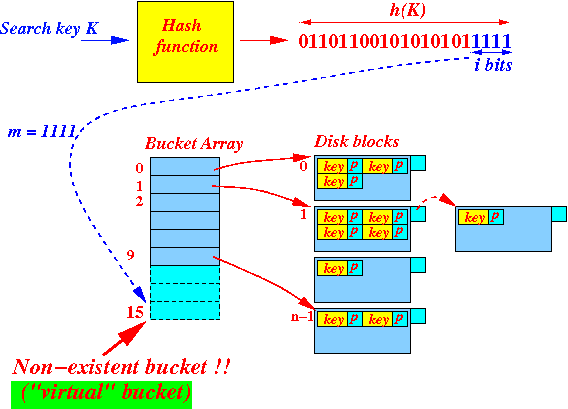
I call a "ghost" bucket = a non-existing bucket !!!
- Mapping "ghost" buckets:
- We use the Suffix-1( )
mapping function
to
map
a ghost bucket:
if ( x ≤ (n − 1) ) { Use: Bucket[ x ] to find the physical hash bucket } else { // "ghost" bucket !! Use: Bucket[ Suffix-1(x) ] to find the physical hash bucket }
- Important Note:
Parameter: n = current number of buckets in use
i = ⌈ log(n) ⌉
Lookup( x )
{
k = hash(x); // General hash function value
m = last i bits of k; // Linear hash function value
if ( m ≤ n−1 )
{
/* =========================================
m is a "real" bucket
========================================= */
Search (x, recordPtr(x)) in bucket m
(including the overflow block);
}
else
{
/* =========================================
m is a "ghost" bucket
Use Suffix-1(m) to map !!
========================================= */
m' = Suffix-1(m);
// I.e.: m = 1xxxxxxxxxx
// m' = 0xxxxxxxxxx
// Note: m' is a "real" bucket !!!
Search (x, recordPtr(x)) in bucket m'
(including the overflow block);
}
}
|
- Fact:
- We need a
policy to
decide if we
need to
increase
the size
physical hash table
I.e.:
- When do we need to add more disk blocks for hash buckets ???
- We need a
policy to
decide if we
need to
increase
the size
physical hash table
- Commonly used
criteria to
increase
the number of buckets n
in Linear Hashing:
if ( Avg occupancy of a bucket > τ ) { n++; // Increase # physical buckets }
- How to determine
average occupancy of
a bucket:
- We need the following
parameters:
n = current number of buckets in use r = current number of search keys stored in the buckets γ = block size (# search keys that can be stored in 1 block)
- Computation:
Max # search keys in 1 block = γ Max # search keys in n blocks = n × γ We have a total of: r search keys in n blocks r Avg occupancy = -------- n × γ
Example:

- We need the following
parameters:
- Increase criteria in
Linear hashing:
r if ( -------- > τ ) n × γ { n++; }
- Insert Algorithm:
Parameter: n = current number of buckets in use i = ⌈ log(n) ⌉ (= # bits used in RandomNumGen( x ) ) Insert( x , recordPtr(x) ) { k = h(x); // h(x) = RandomNumGen(x) m = k % 2i ; // Last i bits = Linear hash function value /* ----------------------------------------------- Insert (x, recordPtr(x)) in "bucket m" ----------------------------------------------- */ if ( m ≤ n−1 ) { /* ========================================= m is a "real" bucket ========================================= */ Insert (x, recordPtr(x)) into bucket m (if overflow, use an overflow block) } else { /* ========================================= m is a "ghost" bucket ========================================= */ m' = Suffix-1(m); // I.e.: m = 1xxxxxxxxxx // m' = 0xxxxxxxxxx // Note: m' is for sure a "real" bucket !!! Insert (x, recordPtr(x)) into bucket m' (if overflow, use an overflow block) } /* ============================================= Check if we need to adjust n ============================================= */ if ( r/(n*γ) > τ ) { Add bucket n; // Now bucket n is not longer a ghost bucket !!! n' = Suffix-1(n); /* ================================================ Note: Bucket[n'] was also used to store keys that were hashed into the "ghost" bucket n !!! We must re-hash all keys in Bucket[n'] into: Bucket[n'] and Bucket[n] ================================================ */ j = ⌈ log(n+1) ⌉ ; // The range of hash bucket index is now [0..n] // j = number of binary digits to express n for ( every search key k ∈ bucket n' ) do { if ( (last j bits of k) == n ) { move search key k into the new bucket n; } } } }
- Parameters:
Max # search keys in 1 block (γ) = 2 Threshold avg occupance (τ) = 0.85
- Initial State:

Average occupancy:
r 3 ------- = ------- = 0.75 (< 0.85) n × γ 2 × 2
- Insert search key
K such that
h(K) = 0101
- Insert
0101:

Result:

Average occupancy:
r 4 ------- = ------- = 1 > τ (0.85) n × γ 2 × 2
- Insert
0101:
- We must add
an new bucket:
- Add bucket
2 (= 10 (binary)):

- Re-hash the
search keys from
/-----> Bucket 00 Bucket 0 --- \-----> Bucket 10Graphically:

Result:

Average occupancy:
r 4 ------- = ------- = 0.6666 ≤ τ (0.85) n × γ 3 × 2Notice that:
- n = 3 (changed) !!!
- i = 2
(changed) !!!
- We can find 1111 as follows:

Explanation:
- 1111
will lead to
the bucket
11
(using the last i (= 2) bits)
which is a
"ghost" bucket
- The search algorithm will use the real bucket 01 instead !!!
- 1111
will lead to
the bucket
11
(using the last i (= 2) bits)
which is a
"ghost" bucket
Continue example....
- Add bucket
2 (= 10 (binary)):
- Insert search key
K such that
h(K) = 0001
- Insert
0001:

Result:

So: Linear Hashing uses overflow blocks !!!
Average occupancy:
r 5 ------- = ------- = 0.833333 ≤ τ (0.85) n × γ 3 × 2No need too add another bucket.....
Continue example....
- Insert
0001:
- Insert search key
K such that
h(K) = 0111
- Insert
0111:

Result:

Average occupancy:
r 6 ------- = ------- = 1 > τ (0.85) n × γ 3 × 2
- Insert
0111:
- We must add
an new bucket:
- Add bucket
3 (= 11 (binary)):

- Re-hash
search keys from:
/----> Bucket 01 Bucket 01 --- \----> Bucket 11Graphically:

Result:

Average occupancy:
r 6 ------- = ------- = 0.75 ≤ τ (0.85) n × γ 4 × 2Notice that:
- n = 4
(changed) !!!
- Every search key
in the Linear Hash table is
now
identified by their
last 2 bits:

- Add bucket
3 (= 11 (binary)):
- Delete was not discussed in
the text book
- But if you understand
how it works,
you can easily devise
an algorithm to
reduce the
number of buckets
Hint:
- When a bucket is delete,
it becomes a
"ghost" bucket
- If the bucket contains
some search keys,
you will need to
move these
search keys....
Where do you move them ???
- When a bucket is delete,
it becomes a
"ghost" bucket