- This webpage contains the analysis
only for
non-persistent CSMA
- The analysis for 1-persistent CSMA in in the subsequent webpage.
- Definitions:
- Arrival rate λ
=
number of
new messages
that arrives
per time unit
- Offered load (rate) G
=
number of
(old and new) messages
that contend for the channel
per time unit
- Throughput S =
number of messages
that are
successfully transmitted
per time unit
A message is successfully transmitted if its transmission does not collide with any other message transmission.
- Maximum propagation delay τ =
the maximum time needed for
a transmission from any source
to reach all nodes
in the CSMA system
The max. prop. delay τ depends on the length of the cables
- Arrival rate λ
=
number of
new messages
that arrives
per time unit
- Simplifying assumptions:
- All packets have the
same length T
(So the transmission time for any packet is the same duration)
- Assume that the
propagation delay between
any two nodes is equal to
τ seconds
Like this:
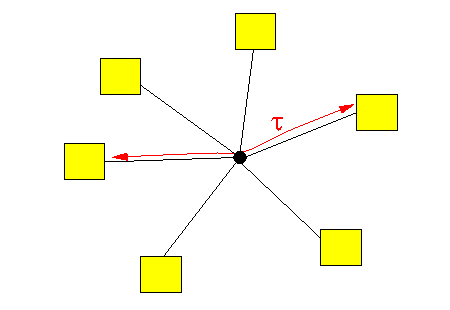
- Define:
τ a = --- Twhich is the normalized propagation delay
- The packet arrival process
is a Poisson process with
rate λ
The offered load (new arrivals and retransmission attempts combined) is also Poisson distributed with rate G
(We will see that the offered load G is dependent on the arrival rate λ)
- All packets have the
same length T
- Abstractly speaking,
the
non-persistent CSMA protocol will
cause the nodes to
transmit in the following manner:
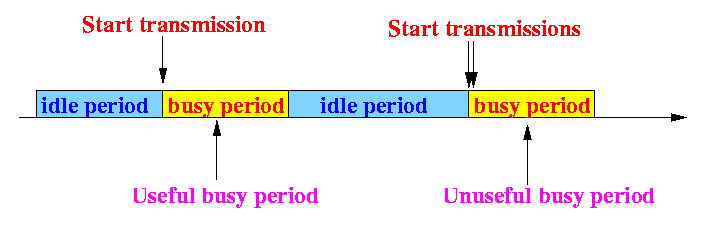
Notes:
- The network is initially
idle
- Then one or more nodes will
transmit
- If one node transmits, then the busy period will contains a successful transmission
- If more than one node transmit, then the busy period will contains a collision (unsuccessful transmission)
Note:
- Because CSMA does not have collision detection, when a node starts transmitting, it will transmit for T sec (until the packet is transmitted)
- After the transmission(s) finishes,
there will be an idle period
when the nodes will
sense the channel
before they transmit.
This idle period has the same characteristic as the first idle period
- The network is initially
idle
- The following diagram gives the
factors that
determine the throughput
of the non-persistent CSMA protocol:

Observations:
- There is a repeating pattern:
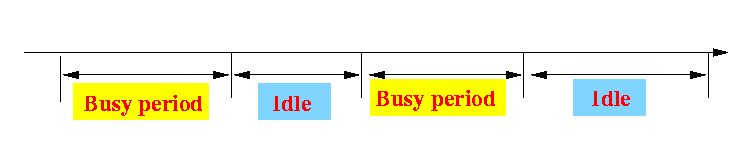
- The length of a
busy period is
variable
(depending on the last starting transmission in the busy period) - The length of an
idle period is
variable (random)
(depending on the time of the next transmission that starts the subsequent busy period)
- There is a repeating pattern:
- Abstraction: represent the repeating pattern by one
average pattern
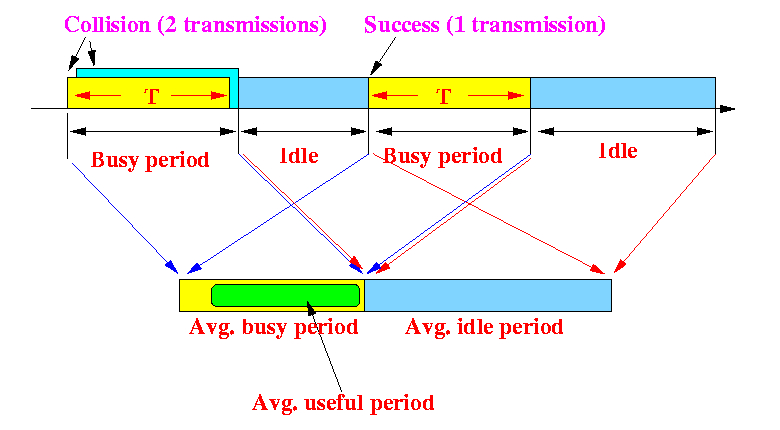
- Definitions and notations:
- B =
the average duration of a
busy period in the
non-persistent CSMA cycle
-
A busy period can be
useful (i.e., successful transmission)
or not useful (i.e., collision)
-
U =
the average duration of a
busy period
that is useful in the
non-persistent CSMA cycle
- I = the average duration of a idle period in the non-persistent CSMA cycle
- B =
the average duration of a
busy period in the
non-persistent CSMA cycle
- Throughput of the non-persistent CSMA protocol:
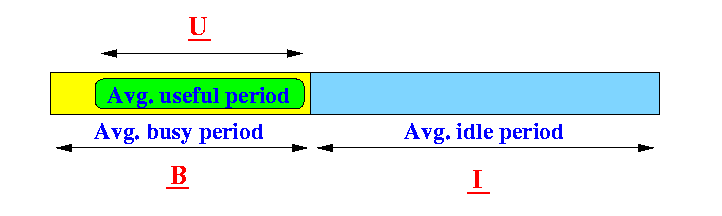
U Snon-persistent CSMA = ------ ...... (1) B + IAll we need to do now is to find U, B, and I :-)
- Characteristics of an idle period:
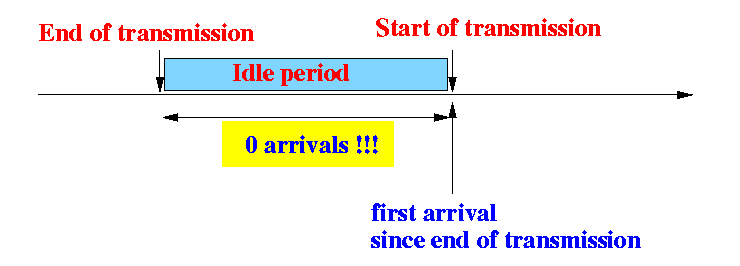
Notes:
- The length (duration)
of an idle period is
a random variable
- The compute the average length of an idle period (random variable) we must first find its probability distribution function (pdf)
- An idle period
ends with
the first transmission
Within the idle period there are 0 message arrivals !
- The length (duration)
of an idle period is
a random variable
- The cumulative density function
of an idle period I is therefore:
Ҏ[ I ≤ x ] = 1 - Ҏ[ I > x ] = 1 - Ҏ[ no packet arrives in x sec ](Gt)k Ҏ[ k arrivals in t sec ] = ---- e-Gt k!
(Gx)0 Ҏ[ I ≤ x ] = 1 - ---- e-Gx 0! <=> Ҏ[ I ≤ x ] = 1 - e-Gx ...... (2)
- The probability density function
of an idle period I is then:
d Ҏ[ I ≤ x ] fI(x) = --------------- d x d (1 - e-Gx) <==> fI(x) = -------------- d x <==> fI(x) = G e-Gx ...... (3)
- Now we can calculate
the average duration I:
I = 0∫∞ x fI(x) dx (= the definition of expected value) <=> I = 0∫∞ x G e-Gx dx 1 | x = ∞ <=> I = -x e-Gx - --- e-Gx | G | x = 0 1 <=> I = ( 0 - 0 ) - ( 0 - --- ) G 1 <=> I = --- ..... (4) GOne down, two more to go....
- Recall that the
length of
each transmission is
equal to T
- 2 kinds of busy periods:
- Useful
- A busy period that contains
exactly one transmission
is useful (no collision)
The length (duration) of a busy period that contains exactly one transmission is equal to T (= length of one transmission)
The contribution of such busy perido to the total useful period is T
- A busy period that contains
exactly one transmission
is useful (no collision)
- Not useful
- A busy period that contains
more than one transmission
is not useful (collision)
The length (duration) of a busy period that contains multiple transmissions is random (and difficult to compute)
However, the contribution of such busy perido to the total useful period is 0 (zero) !!!
- A busy period that contains
more than one transmission
is not useful (collision)
- Useful
- Average length of the useful period:
- The average length of
the useful periods is the following
weight average:
U = T × Ҏ[ transmission successful ] + 0 × (1 - Ҏ[ transmission successful ])
- The average length of
the useful periods is the following
weight average:
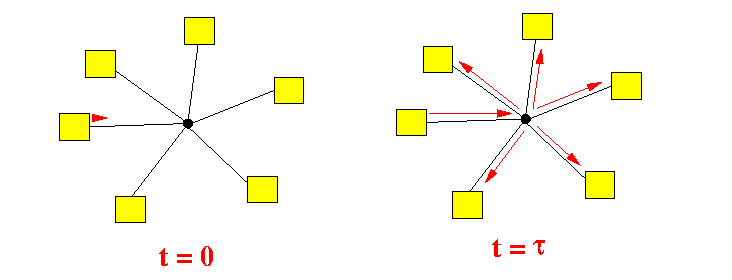
- A busy period is
successful, i.e., contains
exactly one
transmission
if an only if:
Notes:
- Some node starts transmitting
- Within τ sec of the
start of this transmission,
no other nodes
will start a transmission
(Then after τ sec, when a node senses the transmission medium it will detect an on-going transmission and will refrain from starting its transmission)
- Some node starts transmitting
- Thus, Ҏ[ transmission successful ] is equal to:
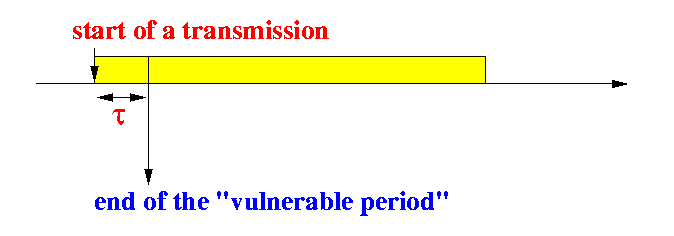
Notes to the figure above:
Ҏ[ transmission successful ] = Ҏ[ 0 arrivals within "vulnerable period" ] = Ҏ[ 0 arrivals within τ sec ](Gt)k Ҏ[ k arrivals in t sec ] = ---- e-Gt k!
(Gτ)0 Ҏ[ transmission successful ] = ----- e-Gτ 0! <=> Ҏ[ transmission successful ] = e-Gτ ..... (5)
- Therefore:
U = T × Ҏ[ transmission successful ] + 0 × (1 - Ҏ[ transmission successful ]) = T × e-Gτ + 0 × (1 - e-Gτ)
U = T × e-Gτ ...... (6)
Two down, one more to go....